GCP: Data Store Deployment
How-to create and register
Prerequisites
- You are an admin in GCP (for steps 1 and 2).
- You are an Account Owner (for step 3).
This guide outlines how to setup a Data Store for storing troubleshooting and temporary data in your GCP cloud.
Steps
Prefer Automation with Infrastructure as Code (IaC)?See the details here to help automate and manage resources from steps 1 and 2 using Terraform.
1. Create a GCS Bucket
Use the GCP Console, CLI or favorite IaC tool to create a new GCS Bucket in your GCP account with no public access. Note that registration (step 3) will fail if the bucket is publicly accessible.
We strongly recommend you do not use an existing bucket or share with other jobs as Monte Carlo might overwrite existing data. And we also recommend the following settings:
- Google-managed encryption
- Expiration lifecycles. 90 days or less for all objects in the following prefixes:
custom-sql-output-samples/
rca
idempotent2. Create an IAM Role and Service Account
First, create a role in the same project as above:
- Under IAM & Admin, go to the Roles section in your Google Cloud Platform console.
- Click the "Create Role" button at the top of the tab.
- Give the new role a name. We recommend "Monte Carlo Data Store".
- Change the Role launch stage to "General Availability".
- Click "Add Permissions" and add the permissions specified below and select "Create".
storage.objects.create
storage.objects.delete
storage.objects.get
storage.objects.list
storage.objects.update
storage.buckets.get
storage.buckets.getIamPolicyNow, create a service account in the same project as above:
- Under IAM & Admin, go to the Service Accounts section in your Google Cloud Platform console.
- Click the "Create Service Account" button at the top of the tab.
- Give the account a name and continue. We recommend "monte-carlo-data-store-sa".
- Click "Done" to complete the creation of Monte Carlo's service account.
- Then navigate to the service account you just created and create a JSON key. A JSON file will download – please keep it safe.
Finally, add the role and principal to the bucket you created above:
- Under Cloud Storage, select the bucket you created in step 1 and navigate to the Permissions tab.
- Select "Grant Access" and fill in the service account you just created as the principal and role you just created as the role. Save changes.
3) Register the Data Store
After creating the bucket and role you can register either via the Monte Carlo UI or CLI.
After this step is complete all integrations that you add to this deployment will automatically use this bucket for storing troubleshooting and temporary data. You can add these integrations as you normally would using Monte Carlo's UI wizard or CLI.
UI
If you are onboarding a new account, you can also register by following the steps on the onboarding screen
- Navigate to settings/integrations/agents and select the
Createbutton. - Follow the onscreen wizard for the "GCP" Platform and "Data Store" Type. The "Bucket name" is the bucket you created in step one and "credentials JSON" are from step two.
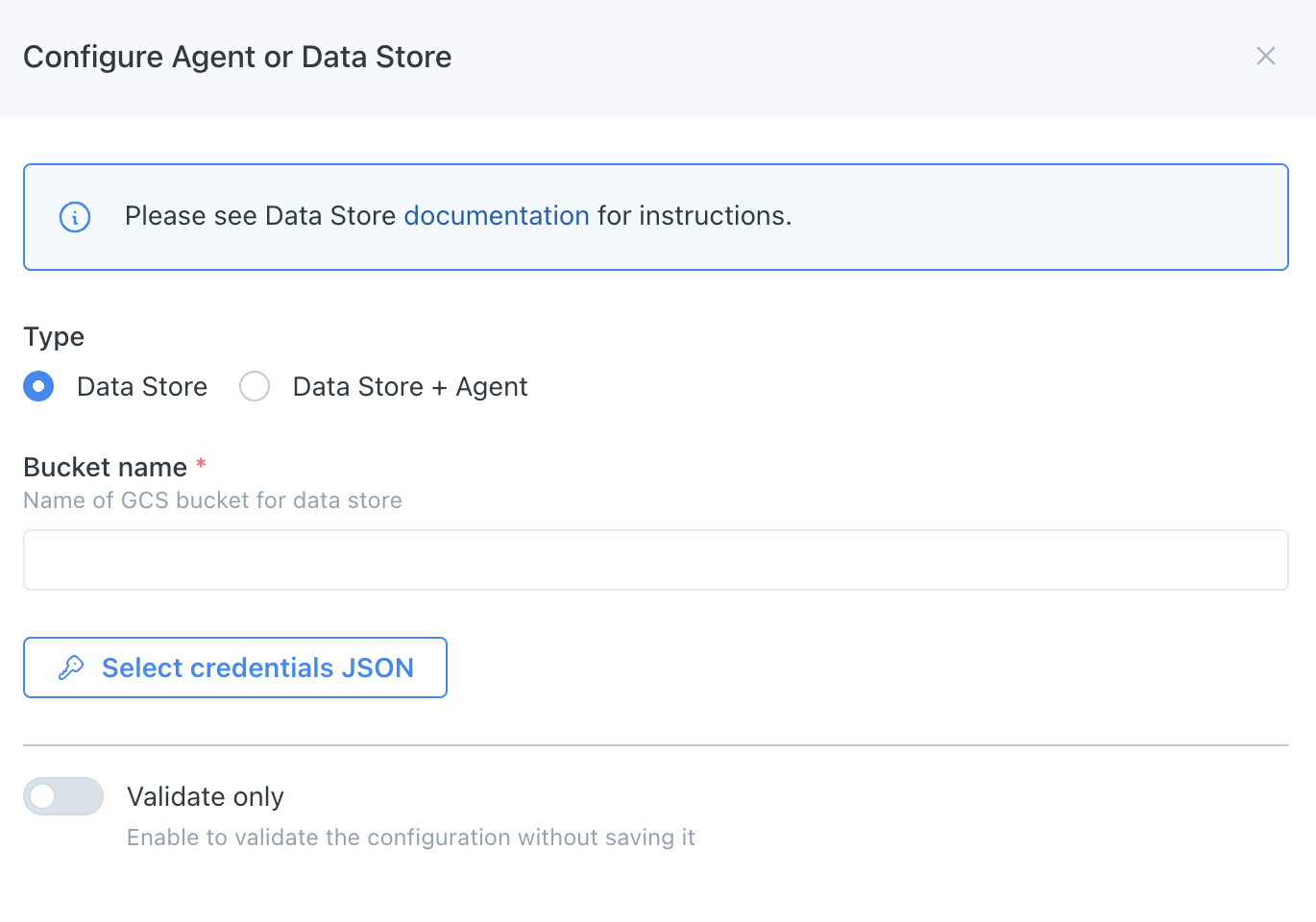
GCP Data Store Registration Wizard
CLI
Use the command montecarlo agents register-gcs-store to register.
For reference on this command please see here. And see here for how to install and configure the CLI.
The bucket-name is the bucket you created in step one and key-file is the service account key from step two.
montecarlo agents register-gcs-store \
--bucket-name example-bucket \
--key-file example.jsonFAQs
Can I deploy resources as code?
Absolutely! This config can be used to automate steps 1 and 2 and manage resources as code with Terraform (source).
If you wish to use it, you can download, review, and then deploy it in your GCP account. Afterwards, please continue with step 3 to register your data store.
Note that this will persist a key in the remote state used by Terraform. Please take appropriate measures to protect your remote state.
Can I further constraint access to this Data Store (GCS Bucket)?
Absolutely! By default this is done via the service account key, but if you prefer you can further restrict requests via an IP allowlist. For instance you can:
- Please refer to the documentation for the list of IP addresses that need to be allowlisted for your platform version.
- Create a new GCP Project for Monte Carlo. We recommend you do not share this project.
- Create a GCS bucket and Role with Service Account in the project created in step #2. You can do this by following the steps here or via this automation.
- Create an Access Level (e.g. via the Access Context Manager) to include the IP address from step #1 and any other IP addresses or members you'd want to be able to administer or access this project.
- Create a Service Perimeter with the Access Level from step #4 and the "Cloud Storage" service. If you prefer you can first create this in "Dry run" mode to validate.
- Continue with registration.
For more information on connectivity, please refer to our Network Connectivity documentation.
How do I check the reachability between Monte Carlo and the Data Store?
Reachability is automatically validated during registration, but you can also use this CLI command or "test" button on the UI to test anytime.
Updated 6 months ago
