Power BI - Credential Creation Process
Step 1: Creating a service principal app:
a. Login to your Azure Portal, and choose App Registrations.
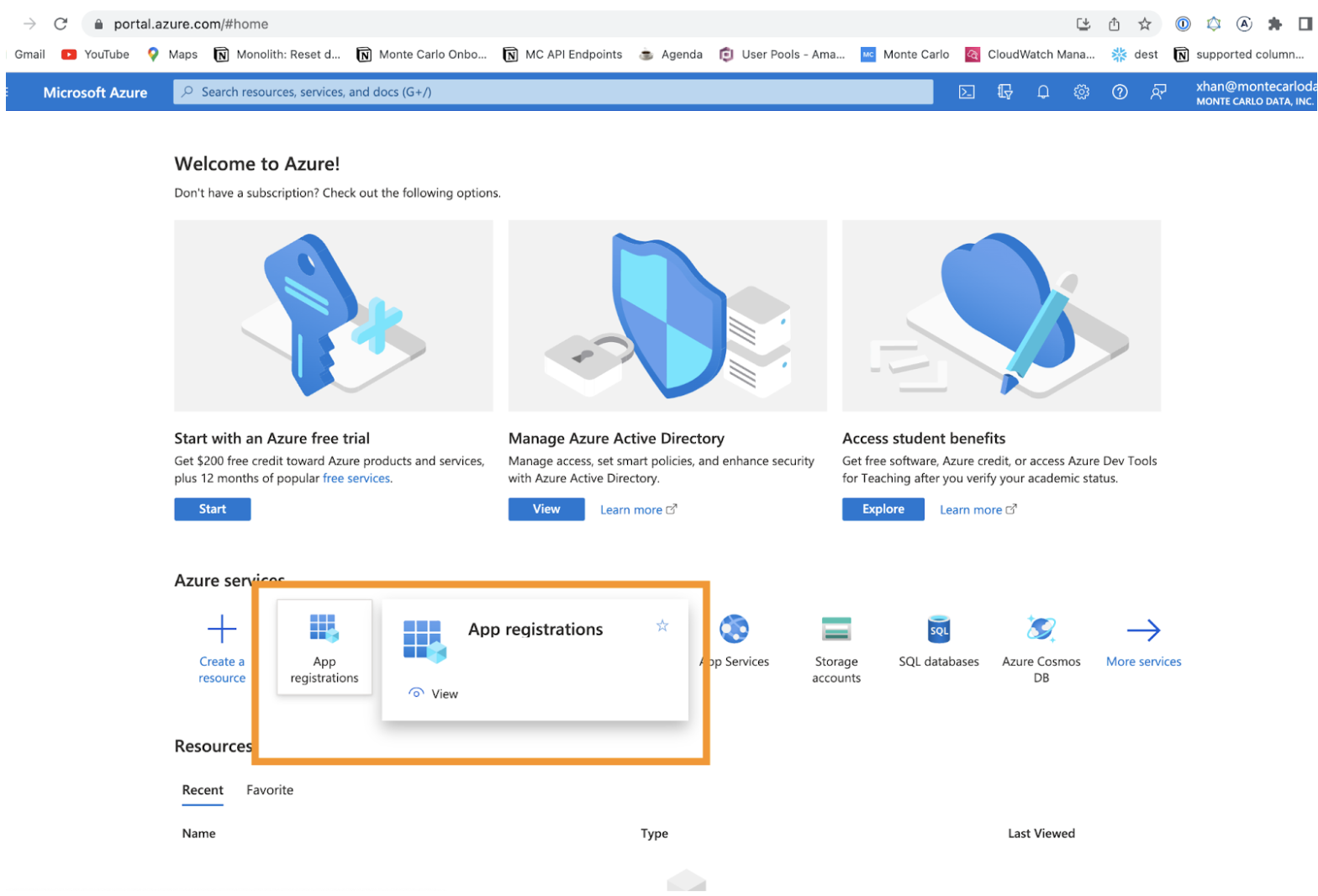
b. Click on the New Registration.
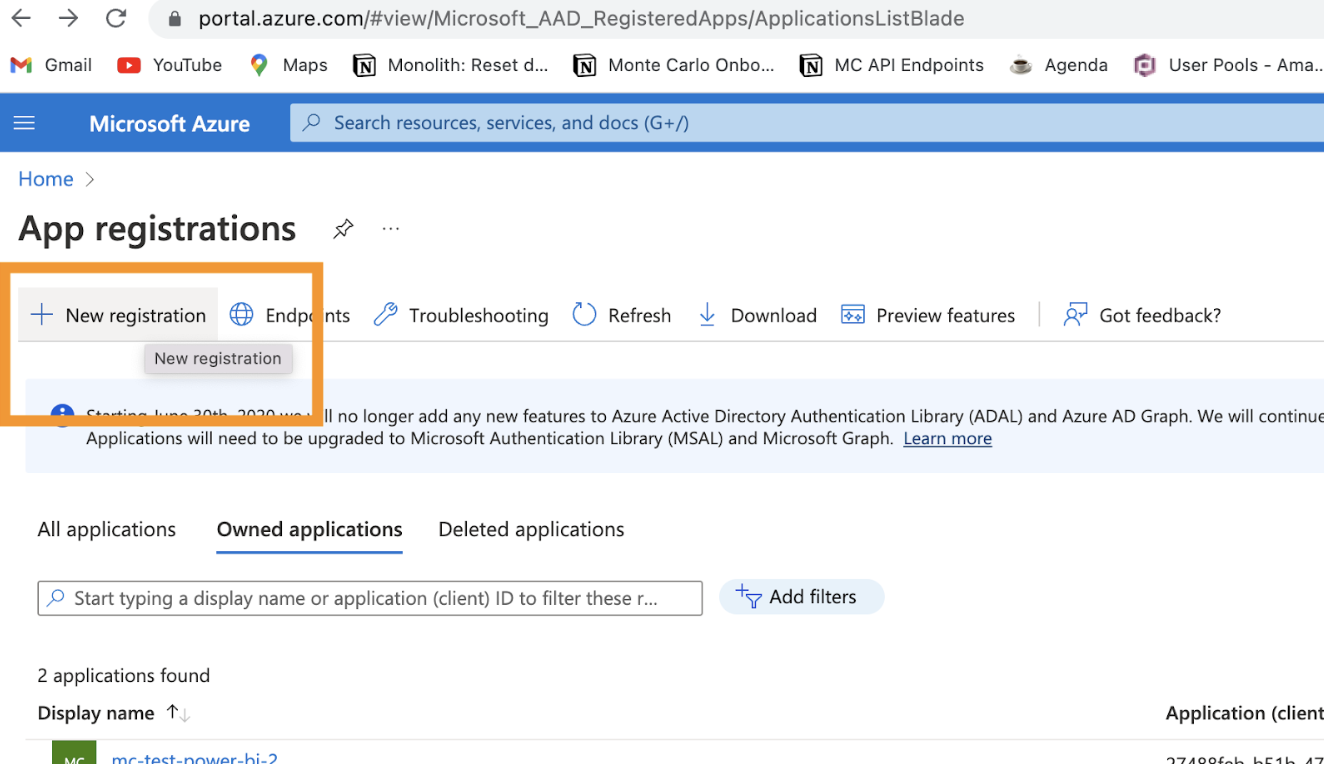
c. In the panel create a new registration for Monte Carlo.
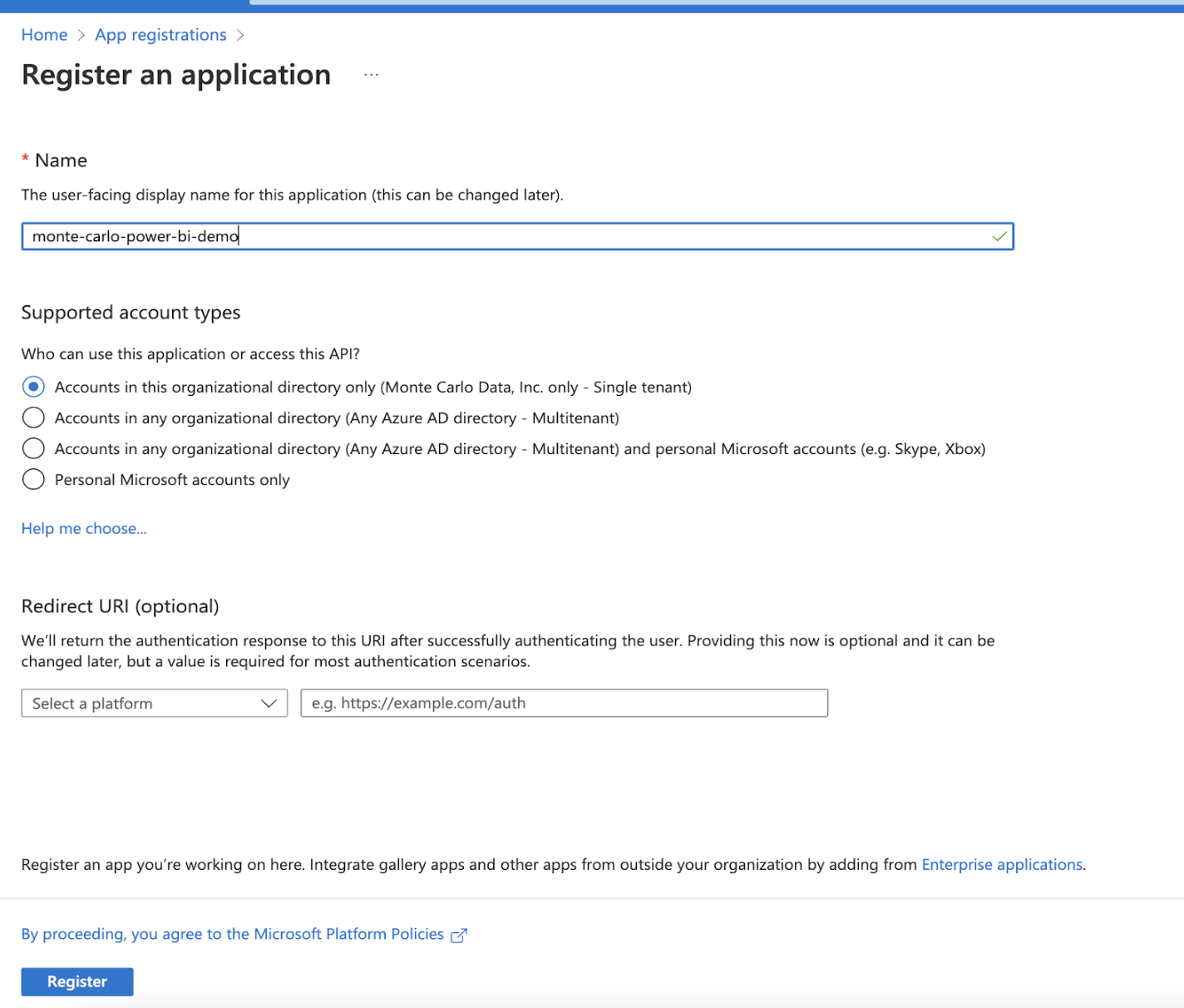
d. After you click the Register button above, a new app is created, it’ll bring you to the application page. Here, we can get the application id (client_id), and you can see the tenant id as well.
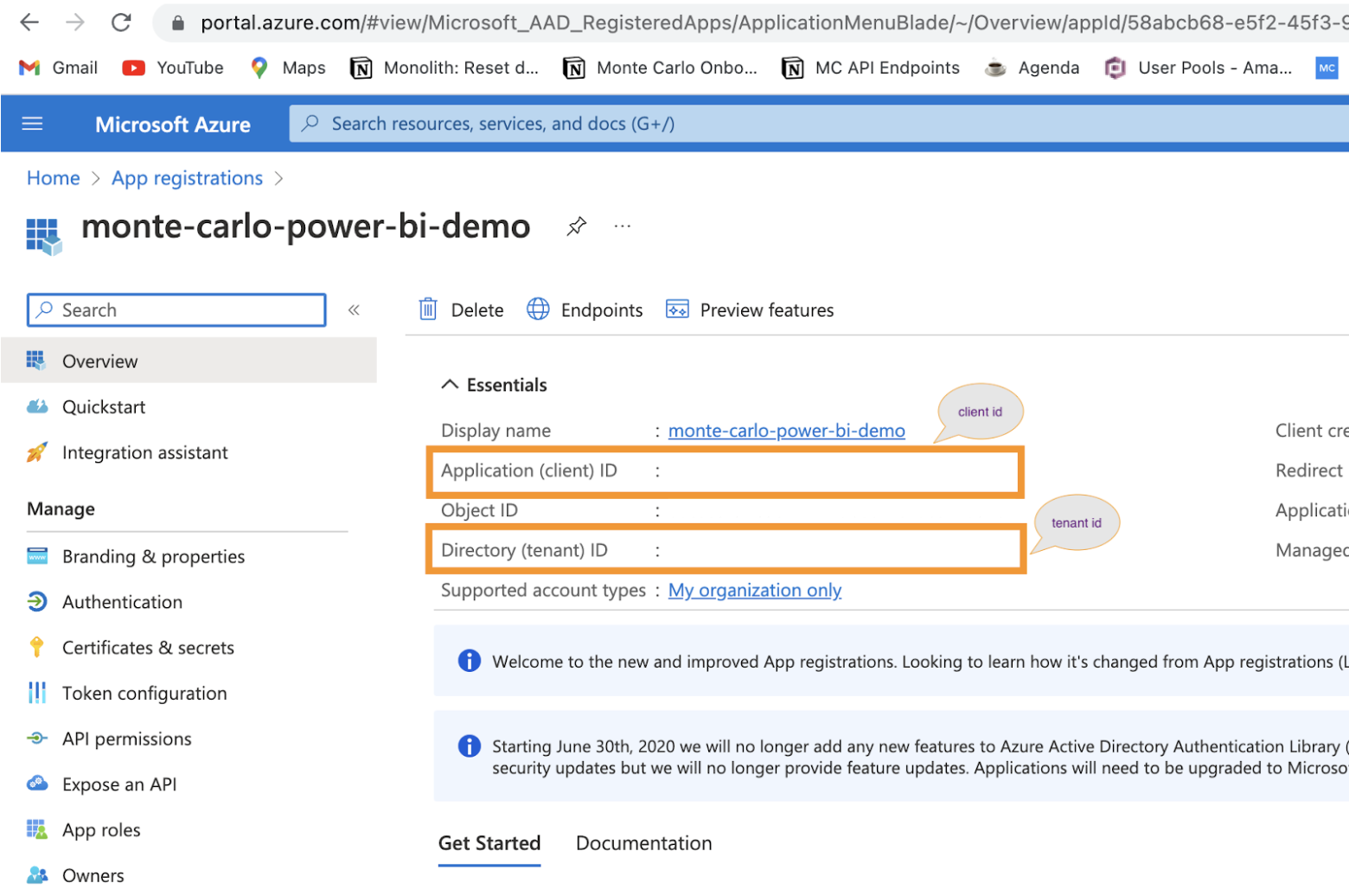
e. Then click on the Certificates & secrets tab to generate a new secret by clicking on the New client secret button.
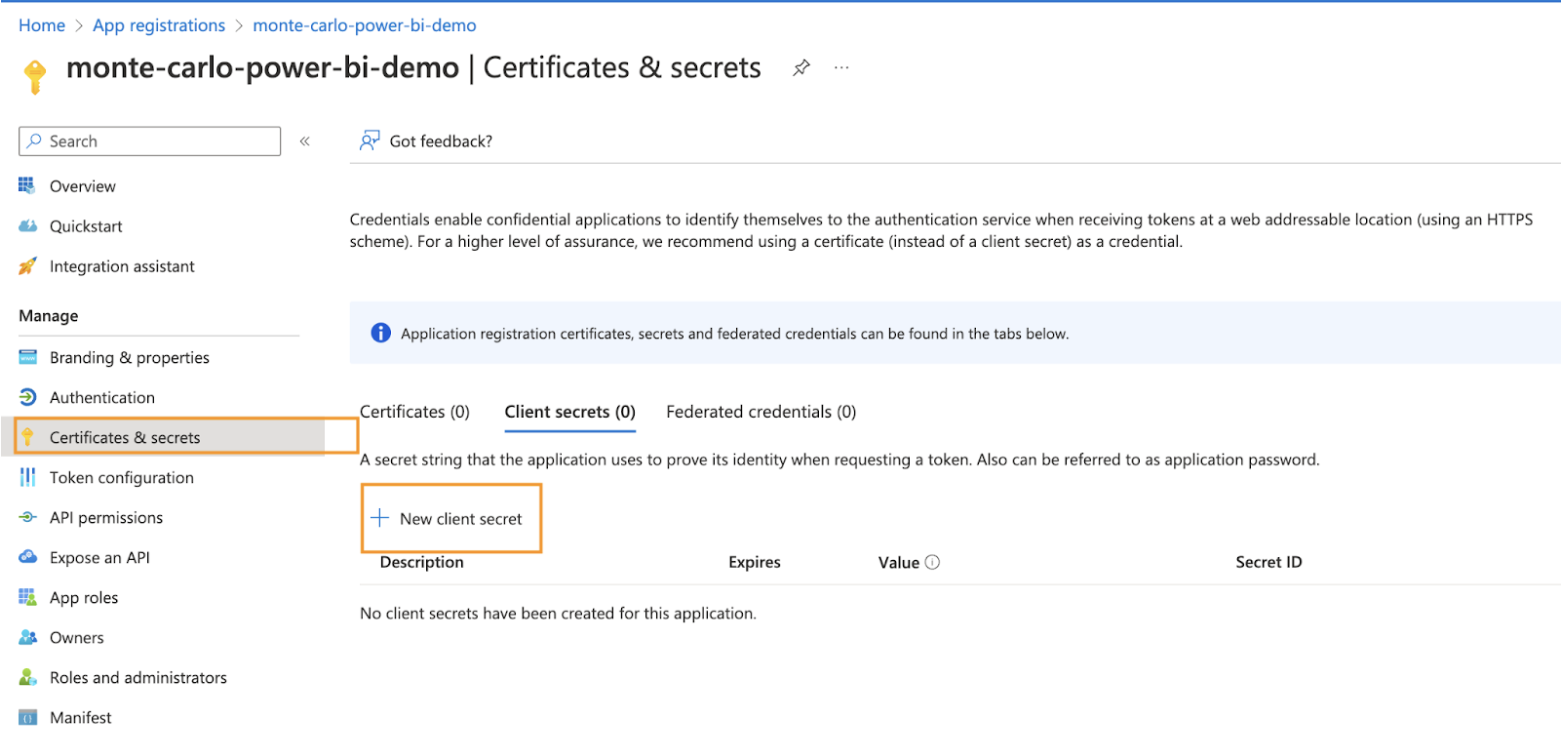
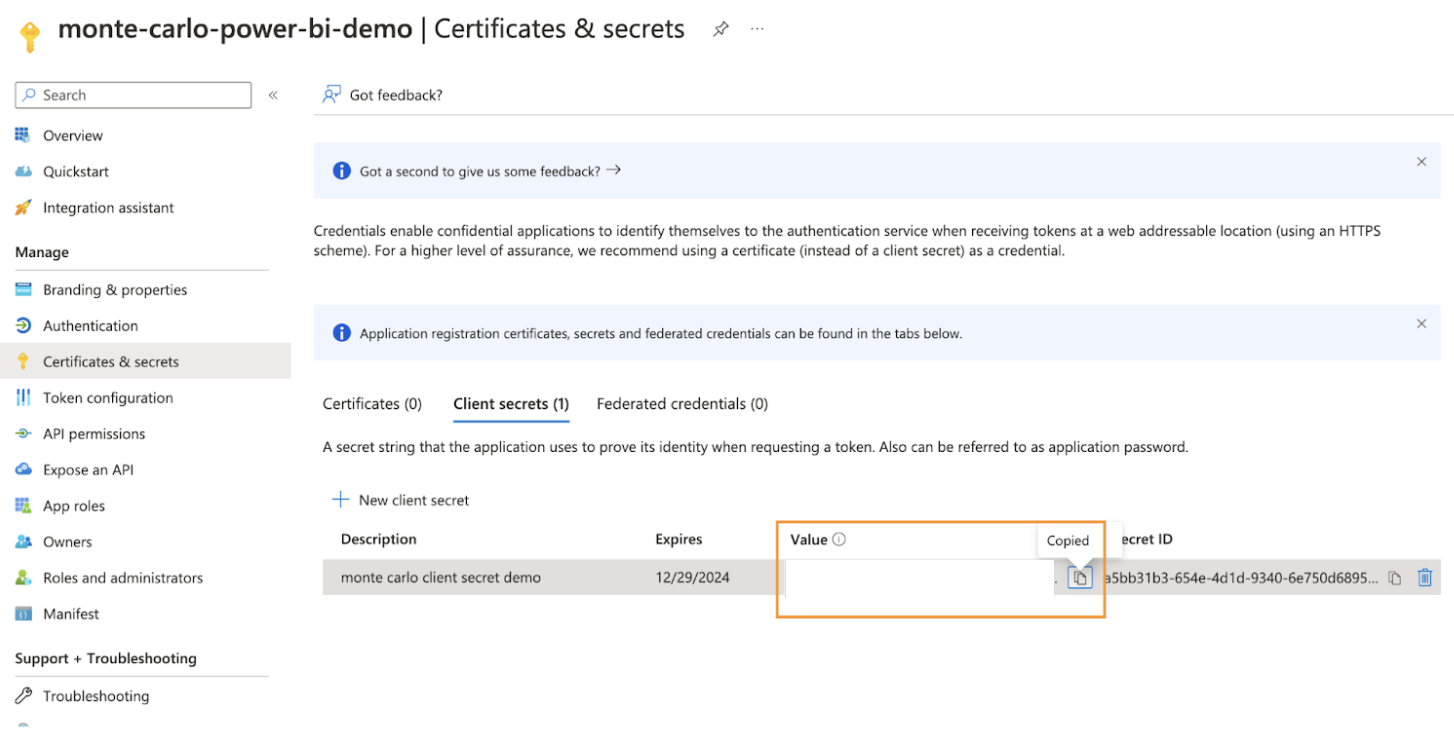
f. Once the secret is created, please copy the value. We’ll use that for auth.
PermissionsThe Service Principal app used for the PowerBI integration must not have any API Permissions configured (eg: Tenant.Read.All or Tenant.ReadWrite.All), as these will conflict with service principal authentication and result in a 401 Unauthorized error when retrieving PowerBI workspaces.
Step 2: Creating a Azure AD security group:
a. Go to the Azure Active Directory.
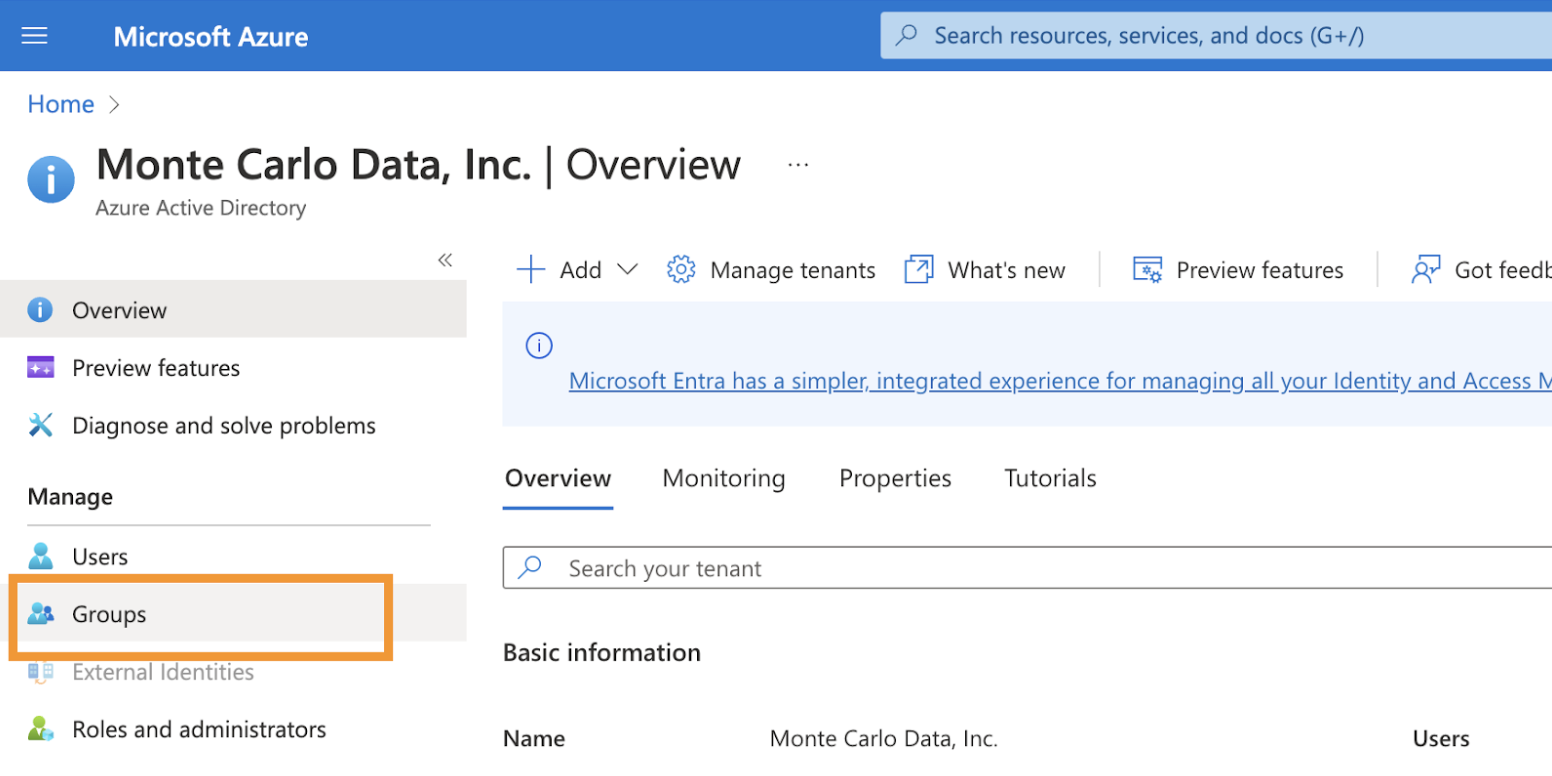
b. Click on the groups.
c. On this page, click the New group button.
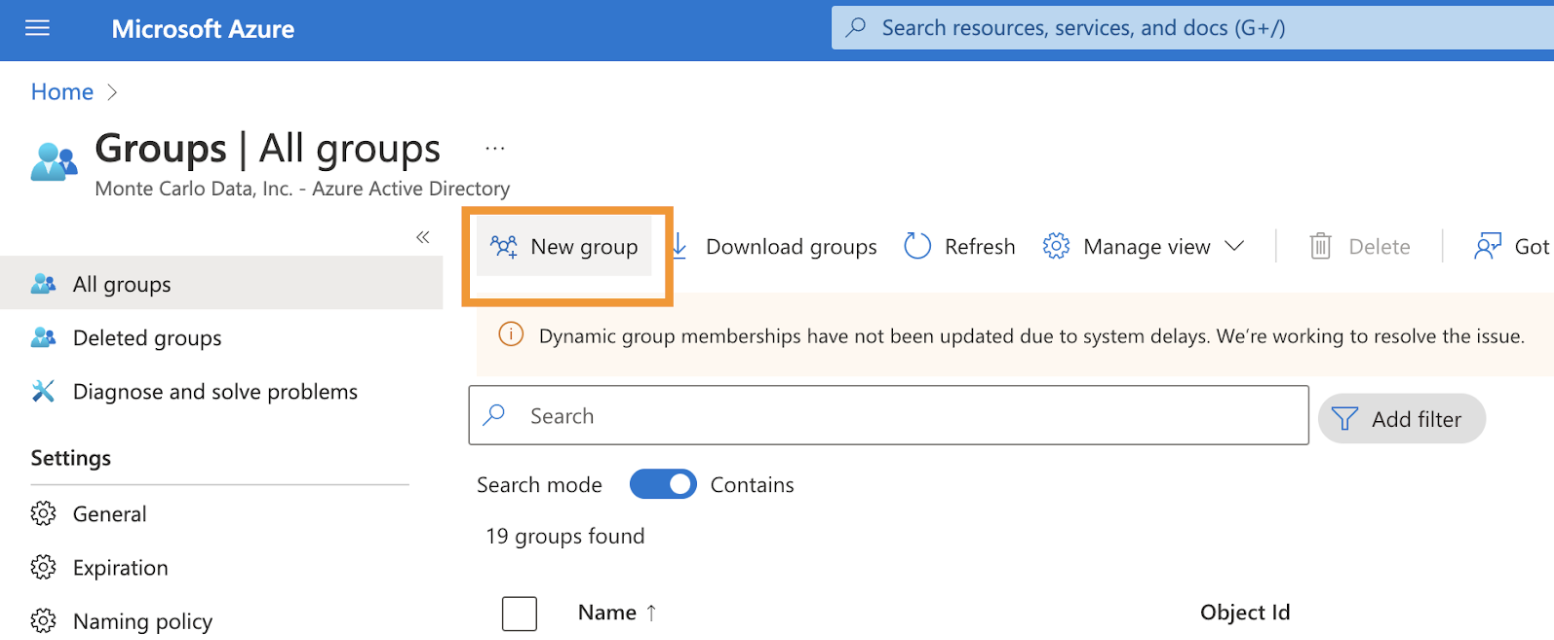
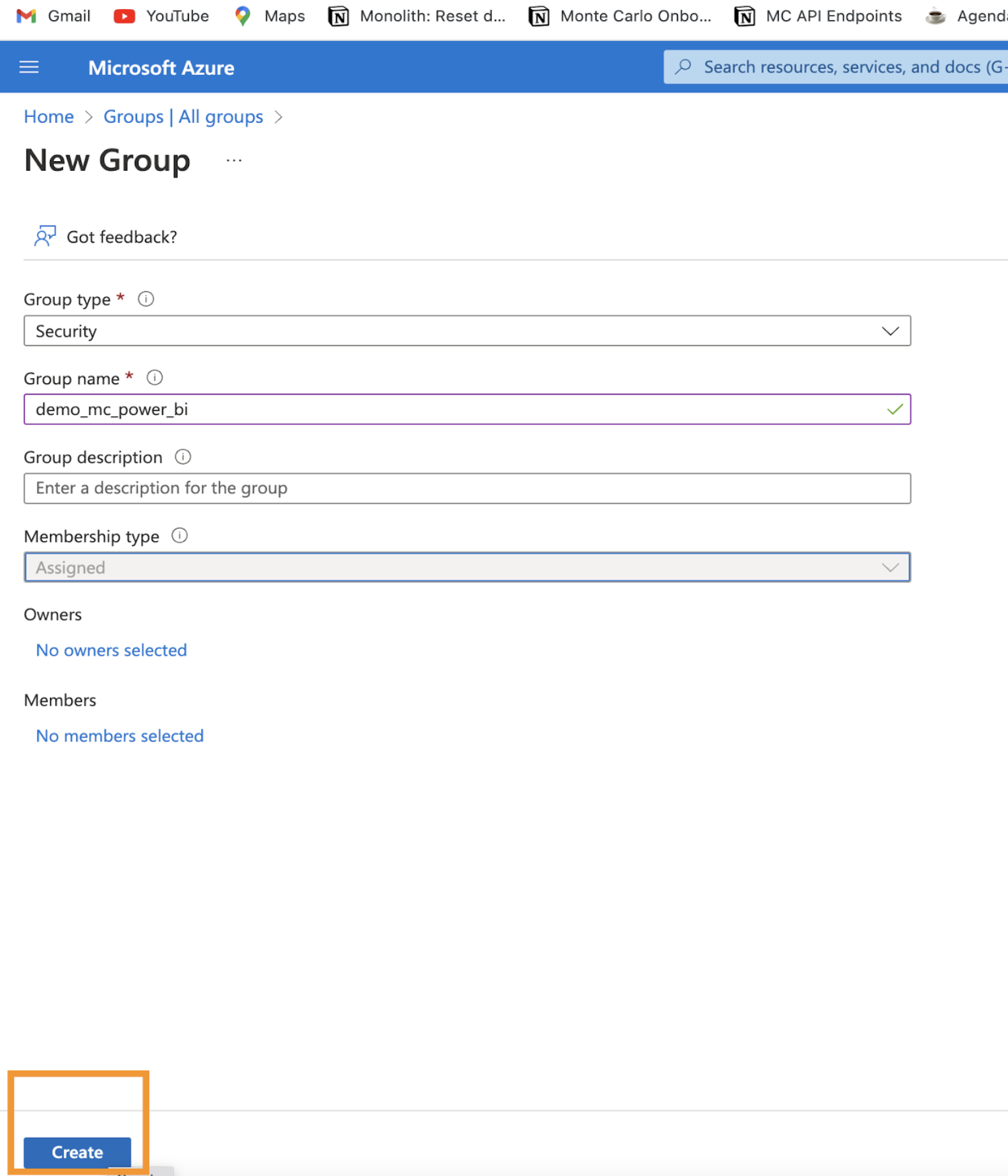
d. Fill the group type and group name and click Create .
e. Click into the new security group you created. And click on the Members tab to add the service principal to this group.
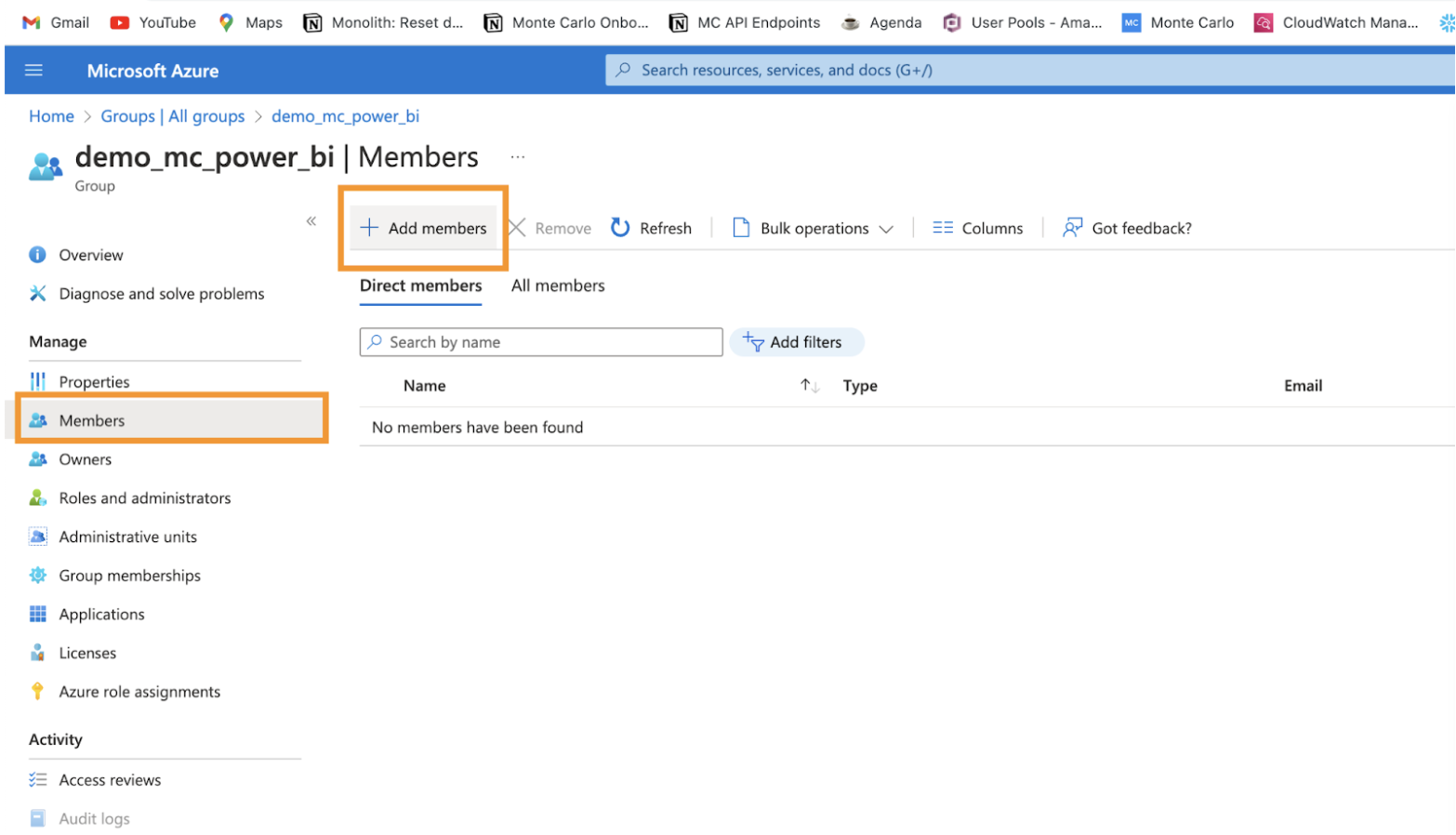
f. Add the service principal you just created in step one as a member of the security group.
Step 3: Grant the access of PowerBI to the security group
a. Go to your power bi website, and go to the admin portal.
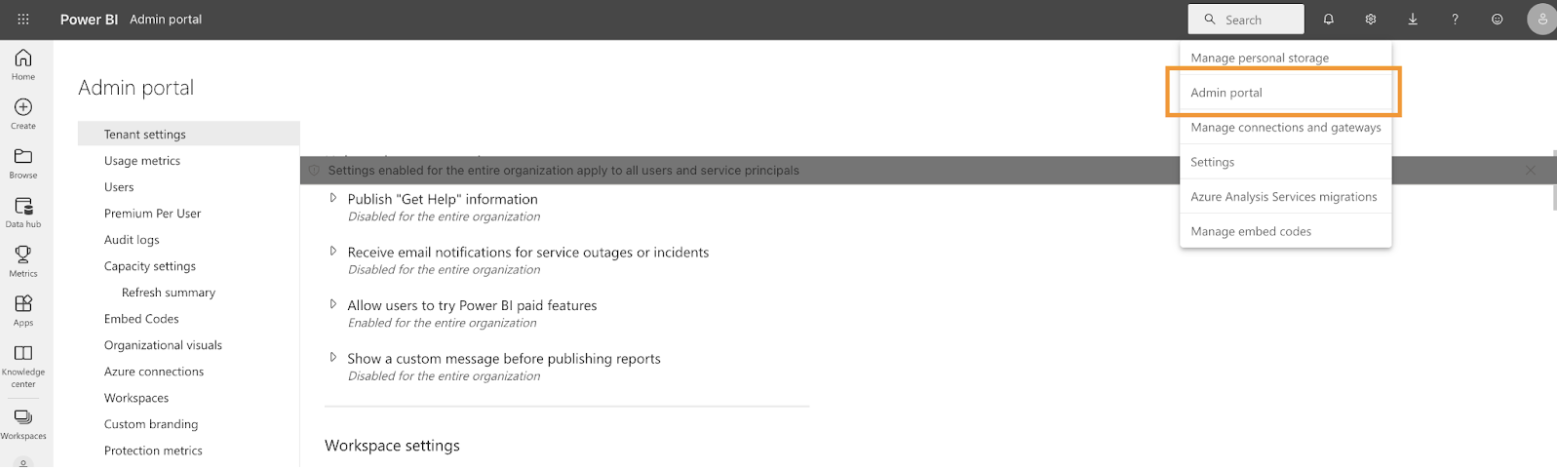
b. Under the Tenant settings. Go to developer settings. Here, you’d enable the Allow service principals to use Fabric APIs. And apply the security group you created in step 2 here. Please choose Specific security groups. And apply the change.
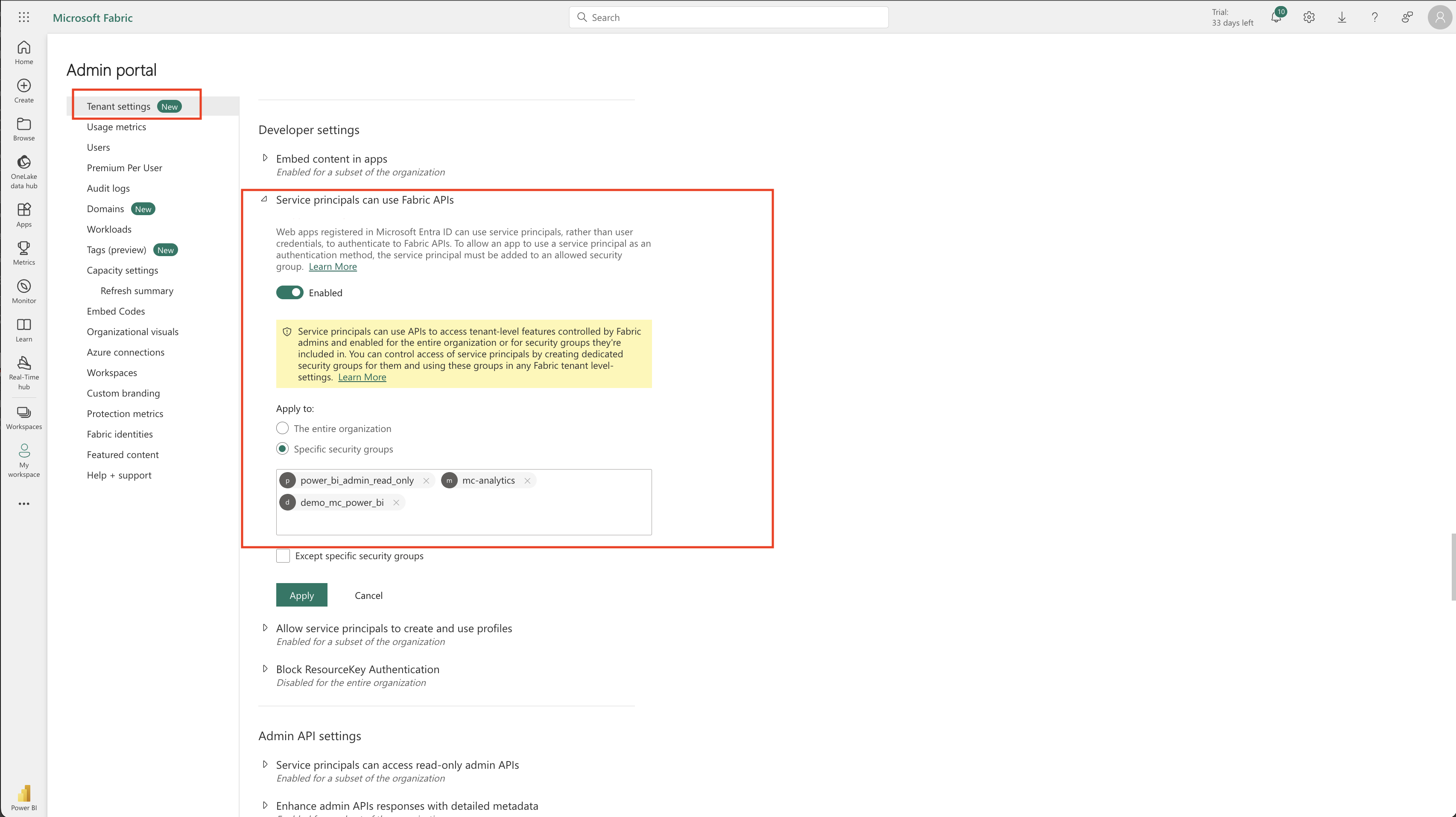
c. Also go to the Admin API settings to enable the service principals to use the admin APIs, enhanced metadata and expressions. Please expand all the panels and enable them, give the security group access to all three of them.
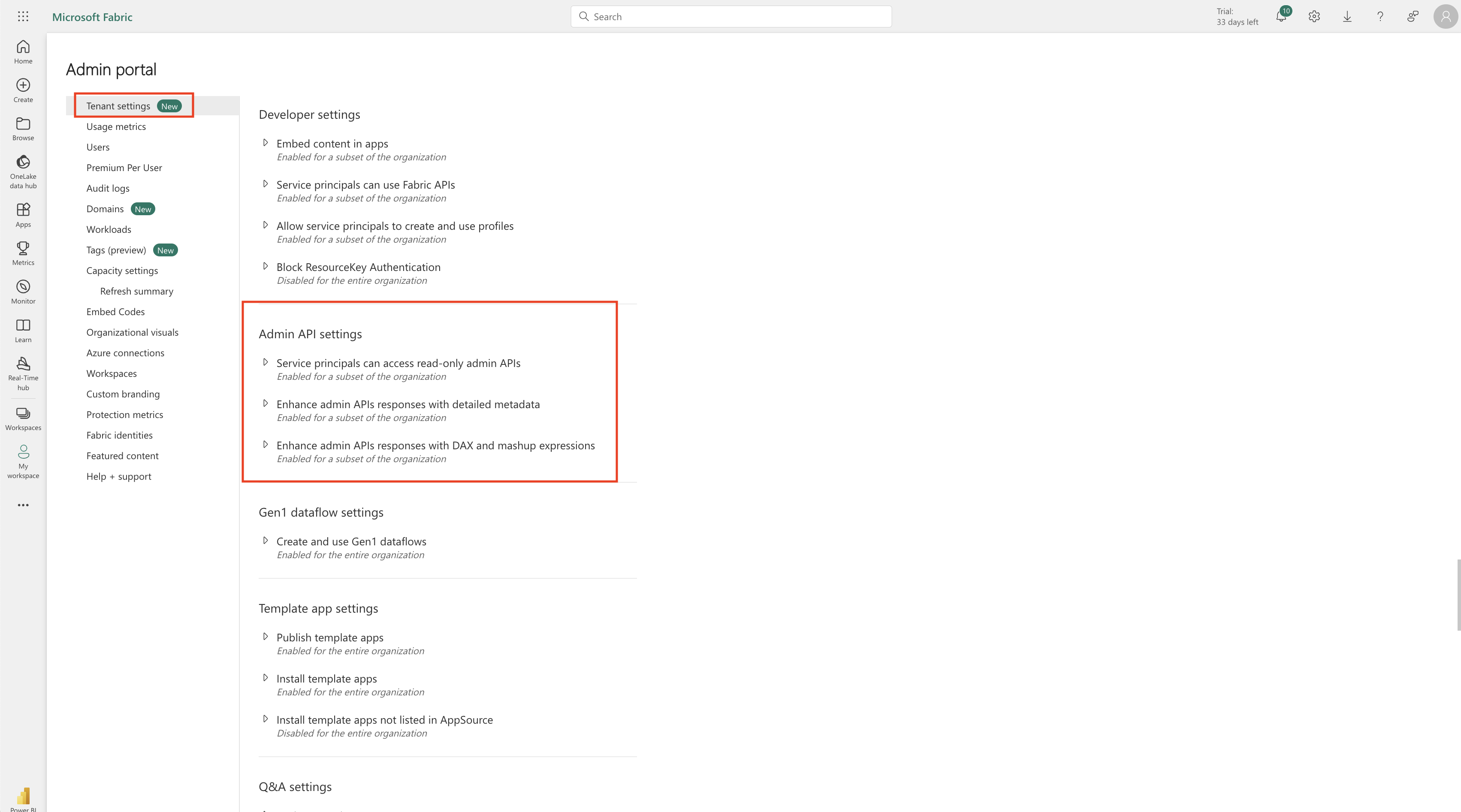
NOTE: The changes take up to 15 mins to be applied. After that you can use the tenant id, application id and secret to set up the integration in Monte Carlo.
Updated 20 days ago
