AWS: Data Store Deployment
How-to create and register
Prerequisites
- You are an admin in AWS (for step 1).
- You are an Account Owner (for step 2).
This guide outlines how to setup a Data Store for storing troubleshooting and temporary data in your AWS cloud.
Steps
1. Deploy
You can deploy the agent either via CloudFormation or Terraform.
Before getting started please review the Monte Carlo AWS account your collection service is hosted in.
When provisioning resources for Monte Carlo deployments on the V2 Platform, use the Collection AWS account id provided in the Account information page. Accounts created after April 24th, 2024, will automatically be on the V2 platform or newer.
If you are using an older version of the platform, please contact your Monte Carlo representative for the ID.
CloudFormation
You can deploy the object storage and associated resources in your AWS cloud using the following quick-create link:
And if you need to share with a colleague or first review the template you can download a copy here (source).
Terraform
This example config illustrates how you can manage data store resources with Terraform.
You can review the full source code here.
2. Register
After creating the bucket and role you can register either via the Monte Carlo UI or CLI.
After this step is complete all integrations that you add to this deployment will automatically use this bucket for storing troubleshooting and temporary data. You can add these integrations as you normally would using Monte Carlo's UI wizard or CLI.
UI
If you are onboarding a new account, you can also register by following the steps on the onboarding screen
- Navigate to settings/integrations/agents and select the
Createbutton. - Follow the onscreen wizard for the "AWS Data Store" Platform type. The relevant values can be retrieved from the CloudFormation/Terraform Outputs for the stack created in step 1. Note that the External ID is required if using this stack.
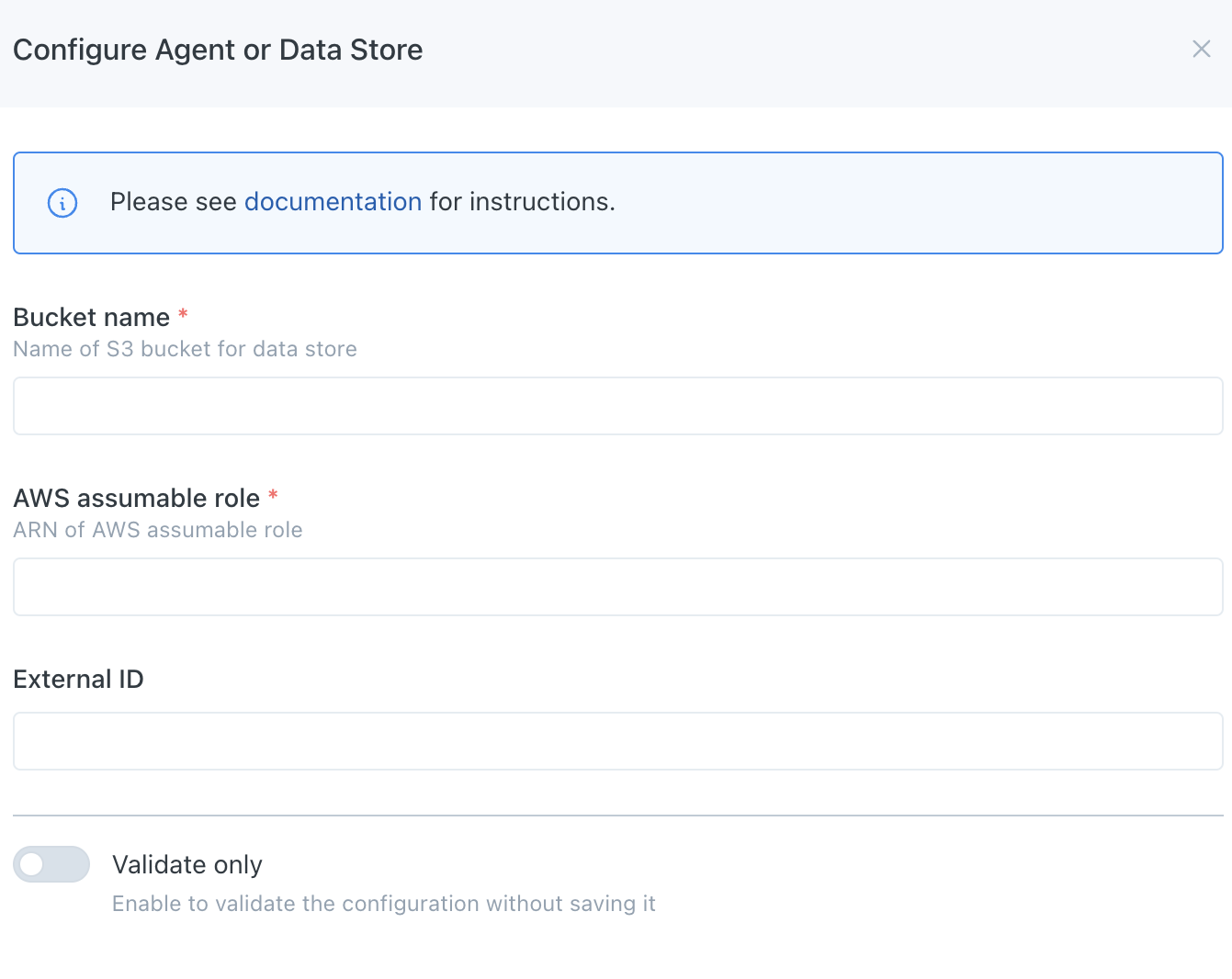
AWS Data Store Registration Wizard
CLI
Use the command montecarlo agents register-s3-store to register.
For reference on this command please see here. And see here for how to install and configure the CLI.
The relevant values can be retrieved from the CloudFormation Outputs for the stack created in step 1. Note that the External ID is required if using this stack.
montecarlo agents register-s3-store \
--bucket-name example-bucket \
--assumable-role arn:aws:iam::123456789:role/mcd-test-apollo-role \
--external-id 1234567890FAQs
Can I further constraint access to this Data Store (S3 Bucket)?
For all deployments on the V2 Platform or newer, Monte Carlo uses VPC endpoints to communicate with AWS Object Storage in supported regions. Additional details and limitations can be found here.
If you wish to constrain this you can update the IAM policy permissions to include a aws:SourceVpce condition using the Data Store VPC endpoint ID provided in the Account information page for your desired region.
For instance, you can add the following element to the s3-policy document:
"Condition": {
"StringEquals": {
"aws:SourceVpce": "<VPCE_ID>"
}
}Note that if you want to use features relying on pre-signed URLs you need to add both of the following statements to the s3-policy document while using this constraint:
{
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::<BUCKET_NAME>/*"
],
"Effect": "Allow",
"Condition": {
"StringEquals": {
"s3:signatureversion": "AWS4-HMAC-SHA256",
"s3:authType": "REST-QUERY-STRING"
}
}
}{
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::<BUCKET_NAME>/*"
],
"Effect": "Allow",
"Condition": {
"StringEquals": {
"s3:signatureversion": "AWS",
"s3:authType": "REST-QUERY-STRING"
}
}
}If your deployment is not on the V2 Platform, you can still further constrain access with the aws:SourceIp condition. Please Reach out to your Monte Carlo representative or support at [email protected] for an IP Address to allowlist. Then, for instance, you can add the following element to the s3-policy document:
"Condition": {
"IpAddress": {
"aws:SourceIp": [
"<IP>/32"
]
}
}For more information on connectivity, please refer to our Network Connectivity documentation.
Can I use server-side encryption with AWS KMS (SSE-KMS)?
Yes! By default, AWS data stores use server-side encryption with Amazon S3-managed keys (SSE-S3), but you can change the default encryption of your bucket to SSE-KMS if you prefer.
First, please review the AWS documentation on using a KMS customer managed key (CMK) with S3. Then:
-
Deploy the AWS data store as documented here. Be sure not to register your data store yet!
-
Identify (or create) the KMS CMK you wish to use by using the console, CLI, IaC, or a tool of your preference.
-
Update the key policy for the CMK from step 2 to include the following statement:
{ "Sid": "MCD_KMS_ACCESS", "Effect": "Allow", "Principal": { "AWS": "<MCD_ ASSUMABLE_ROLE>" }, "Action": [ "kms:Decrypt", "kms:GenerateDataKey", "kms:DescribeKey", "kms:Encrypt", "kms:ReEncrypt*" ], "Resource": "*" }Be sure to replace
<MCD_ASSUMABLE_ROLE>with the assumable role ARN (ObjectStoreRoleArn). The relevant value can be retrieved from the CloudFormation outputs for the stack created in step 1. -
Update the default encryption type for the bucket created in step 1 from
SSE-S3toSSE-KMS.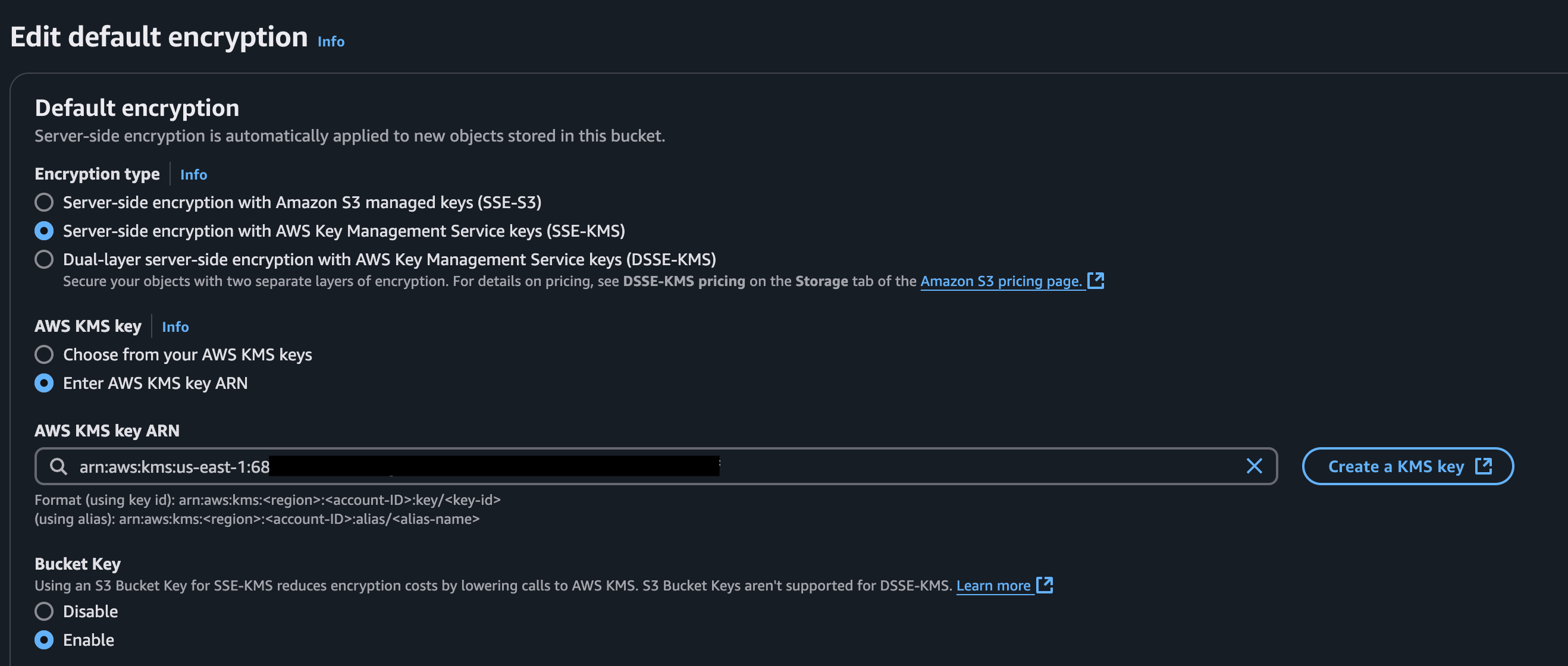
AWS Console Example
The bucket name can be retrieved from the CloudFormation outputs for the stack created in step 1 (
ObjectStoreBucketName). You can do this using the console, CLI, IaC, or a tool of your preference. -
Proceed to register the data store with Monte Carlo as documented here.
How do I check the reachability between Monte Carlo and the Data Store?
Reachability is automatically validated during registration, but you can also use this CLI command or "test" button on the UI to test anytime.
What does the folder structure look like for the data store?
All data store types use a similar folder structure. Below is a high-level overview of the purpose of each folder:
custom-sql-output-samples: Stores custom SQL query results or samples.rca(orrca-results): Stores RCA data samples for other monitor types.idempotent: Stores temporary operational data for the data store.
Updated about 2 months ago
