SCIM
Overview
The System for Cross-domain Identity Management, or SCIM, is an open standard that allows for the automation of user and group provisioning. With SCIM you can automatically provision and deprovision users and authorization groups in your Monte Carlo account by syncing with your organization’s identity provider (IdP).
Key Features
- Create users in Monte Carlo when they are provisioned to Monte Carlo in your IdP
- Remove users in Monte Carlo when they no longer have access to Monte Carlo in your IdP
- Keep user attributes like first and last name synchronized between your IdP and Monte Carlo
- Manage authorization groups and their user membership in Monte Carlo by synchronizing groups from your IdP
Supported IdPs
Currently Monte Carlo supports SCIM provisioning with the following IdPs:
- Okta
- Microsoft Entra ID
Set-up
You must be an Account Owner in Monte Carlo to enable SCIM provisioning
The set up for SCIM provisioning requires enabling SCIM in your Monte Carlo account first and then enabling SCIM provisioning in your IdP. To enable SCIM in your Monte Carlo account:
1. Navigate to Settings -> Users -> SCIM
2. Select "Add" and fill out the required fields
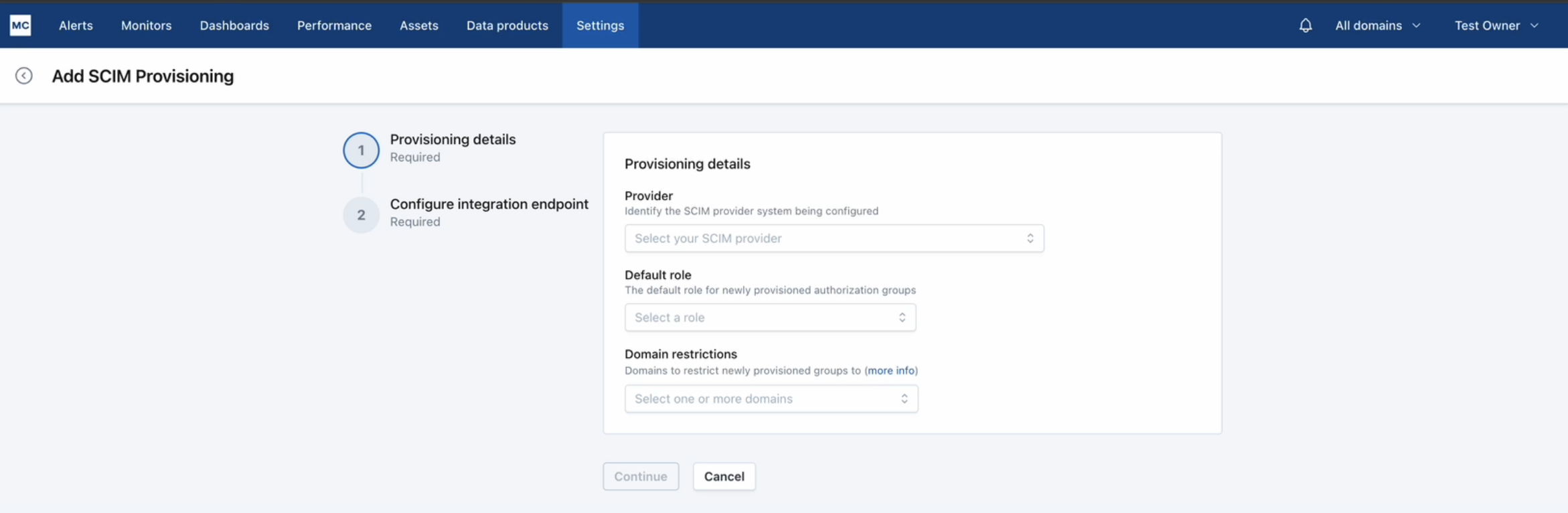
- Provider: The type of Identity Provider being used for SCIM provisioning
- Default Role: If you enabled group sync, this will be the role assigned to any new authorization groups created from SCIM requests. This will apply to authorization groups that had not already been mapped in Monte Carlo. Role assignment can be updated in "Users"-> "Authorization groups" anytime.
- Domain restrictions[Optional]: If you enabled group sync, domains added here will be assigned to any new authorization groups created from SCIM requests. This will apply to authorization groups that had not already been mapped in Monte Carlo. Domains assignment can be updated in "Users"-> "Authorization groups" anytime.
3. Configure Integration Endpoint
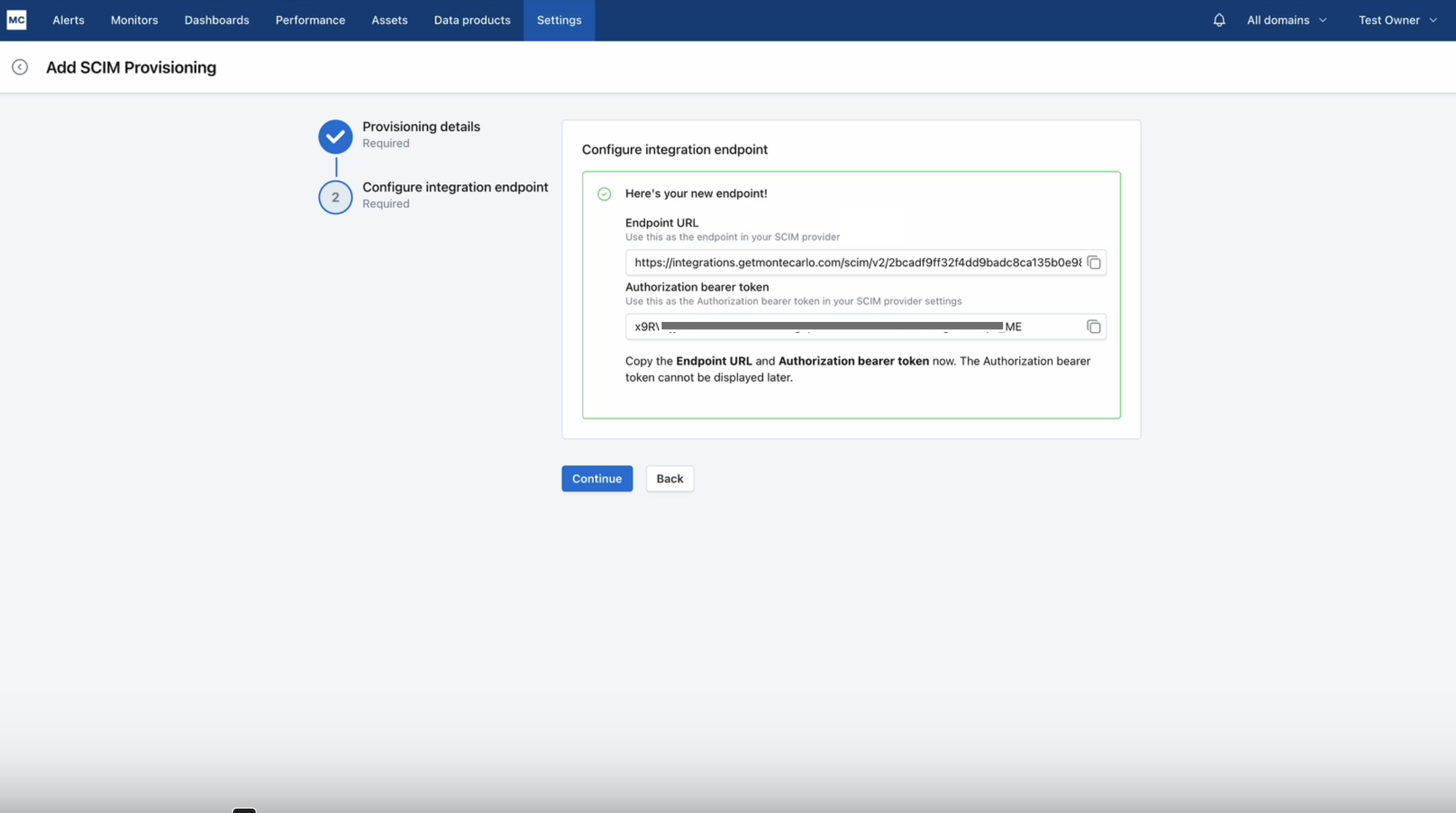
After selecting 'Continue' you will be presented with an Endpoint URL and bearer token. Copy both of these values as you will need to provide them to your IdP.
4. Configure SCIM Provisioning in your IdP
Now that you have your endpoint URL and token, you can enable SCIM provisioning in your IdP. Follow the guide for the IdP your organization uses:
Setting up SCIM Provisioning with Okta
Setting up SCIM Provisioning with Microsoft Entra ID
Network Access Control
You can restrict access to the SCIM v2 endpoint by IP address using Network Access Control Lists. See Network Access Control for setup and configuration details.
FAQs
- What is the purpose of the default role and domain restrictions in the provisioning details?
If you enable group sync from your IdP, your IdP can create authorization groups in Monte Carlo and assign users to those groups. The default role and domain restrictions [optional] that you select when enabling SCIM in Monte Carlo will be assigned to any authorization groups created in your account through SCIM. - Can I edit an authorization group once it has been created?
Yes. Once an authorization group has been created through SCIM, you can choose to edit the role and/or domain assignments for that group. - What happens if I enable SCIM provisioning but I already have users and authorization groups created in Monte Carlo?
When enable SCIM provisioning in your IdP and the initial sync happens, the IdP will first check if the user or group already exists in Monte Carlo. For users uniqueness is based on the email field, for groups it is based on the authorization group name.
If the user or group already exists, your IdP will link its user/group to Monte Carlo’s ID. Any changes to that user or group will be synced to Monte Carlo moving forward.
If the user or group does not already exist, your IdP will create it in Monte Carlo and then sync the IDs together. - What happens if I disable SCIM provisioning in only Monte Carlo?
If SCIM provisioning is disabled in your Monte Carlo account, all SCIM requests from the IdP will be rejected. Note that most IdPs have a retry policy and will periodically retry the failed requests. Disabling SCIM in MC could be helpful if you want to temporarily stop requests while fixing an issue but for long term disabling of SCIM it is recommended to disable through the identity provider. - How soon will users and group show up in Monte Carlo?
Monte Carlo will create, update or destroy users and groups as soon as the SCIM request is received. The frequency in which your IdP syncs with Monte Carlo will determine how quickly users or groups appear in Monte Carlo. This can range from instantly to every 40 minutes depending on the IdP. - Do I have to be using SSO to use SCIM?
No. If you are not using SSO, when a user is created from a SCIM request that user will need to go to https://getmontecarlo.com/signin/ and use the ‘forgot password’ flow to gain access to the account.
If you are using SSO, users can sign in with SSO any time after they have been added to the IdP application. - Can I choose to sync only users and not groups?
Yes. Monte Carlo supports syncing users and groups from your IdP but you do not have to enable both. When enabling SCIM provisioning in your IdP you will have the option to enable user and/or group syncing.
Updated 7 days ago
