Deploying the Collector
DeprecatedAs of January 2024, the Monte Carlo Data Collector Deployment Model has been deprecated in favor of the Agent and Object Storage Deployment models. Please see Architecture & Deployment Options for more information.
To deploy the data collector in your AWS environment, you will:
- Obtain your account's data collector template by signing up to Monte Carlo.
- Create the data collector CloudFormation stack in your AWS account.
If you do not wish to host the data collector in your environment, please contact your representative to deploy it in Monte Carlo's environment.
Obtaining your CloudFormation template
- Please create your Monte Carlo account by visiting the sign up page. If someone else on your team has already created an account, please reach out to them to obtain the template.
- Follow the onboarding steps to reach the "Install data collector" step, where you will have a link to your account's CloudFormation template. Please note: the link is specific to your account and cannot be shared across accounts.
- You can select the desired AWS region you want the Data Collector hosted in by using the combo-box in the upper right corner.
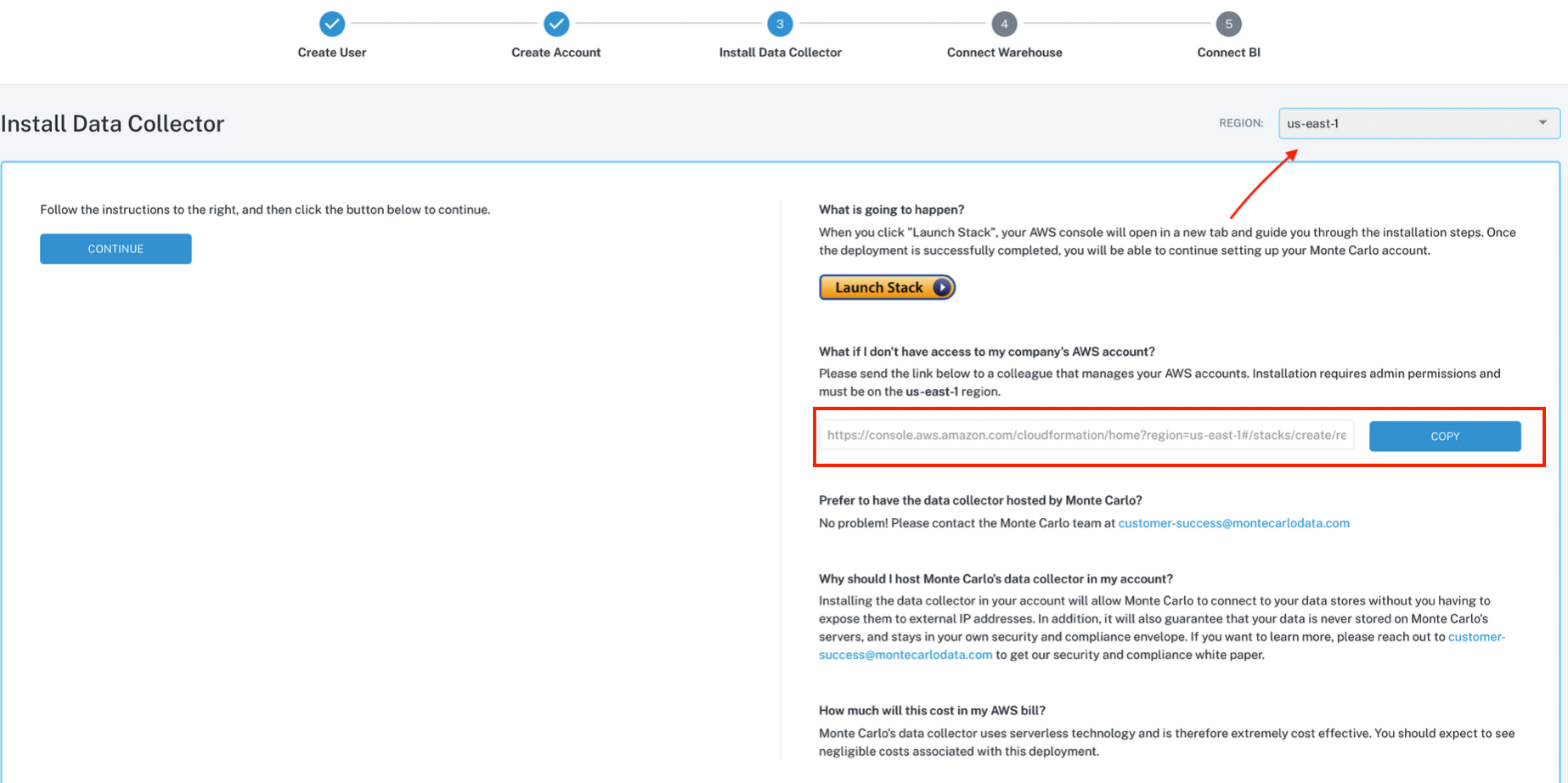
Obtaining a link to your account's data collector CloudFormation template
Creating the collector's stack in your AWS account
- Please make sure you are signed in to the AWS console for the account which will host the data collector.
- Copy the link provided by Monte Carlo and paste it in your browser. In the page that opens, please name the CloudFormation stack, configure advanced options if necessary and click "Create Stack" to deploy it.
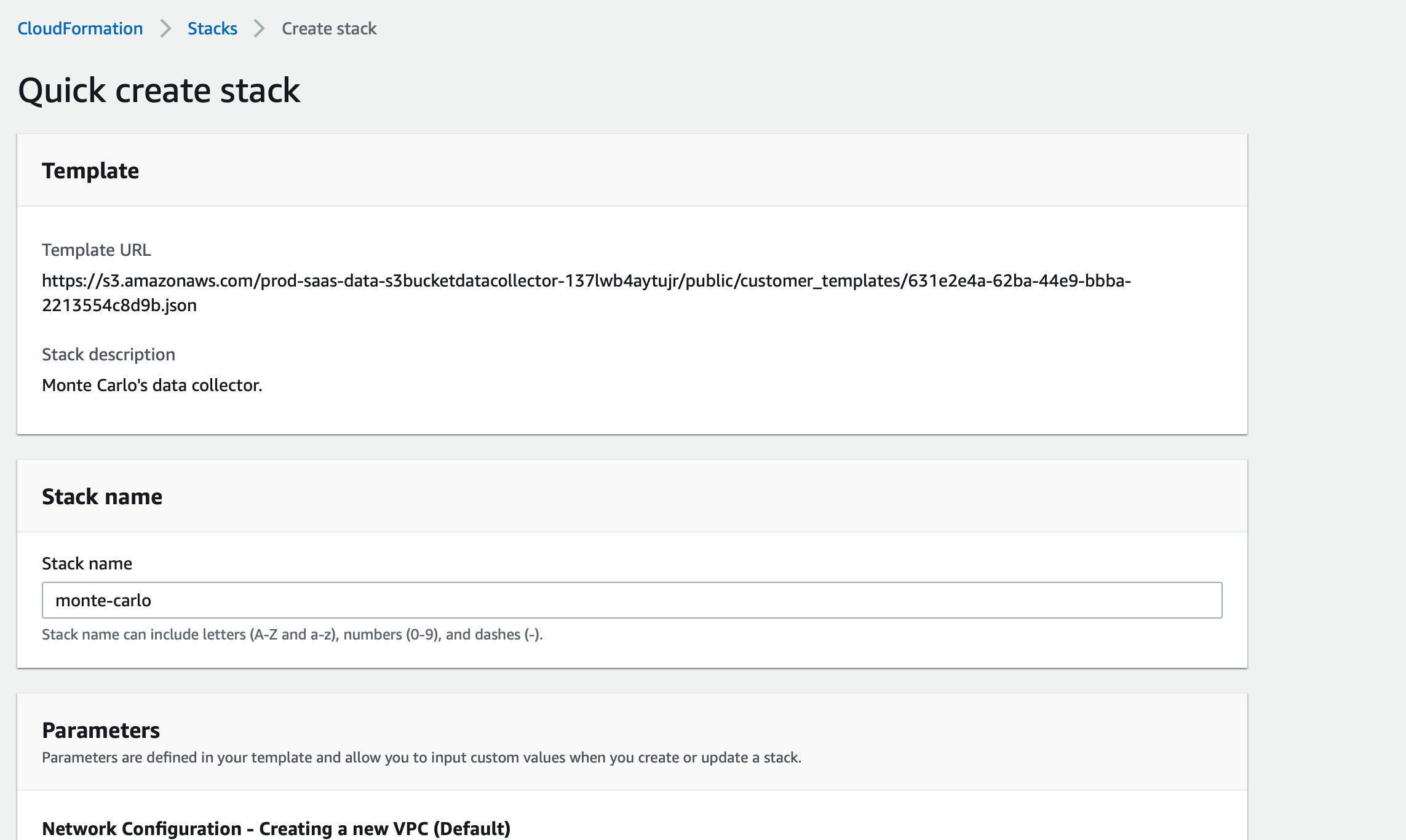
Creating the data collector stack
Advanced options
The data collector defaults to the most common setup, and most customers will keep the pre-populated default parameter settings when deploying its stack.
The following configurations are available for customized setups:
Scenario | Template parameters to edit |
|---|---|
I need to peer the collector's VPC with a VPC that overlaps with 10.0.0.0/16 |
|
I need to deploy the collector into an existing VPC in my account |
|
I need to remove the cross-account role / function that allows remote upgrades of data collector code |
|
I want to enable access logging for the gateway This requires having an account-level IAM role in the same region as the collector, which allows writes to CloudWatch before enabling. See here for details on how to setup the role. |
|
I am going to integrate Monte Carlo with a Hive/Glue-based data lake |
|
I want to customize the default retention period for troubleshooting and temporary data in the data collector |
|
I want to generate and use a KMS CMK (i.e. SSE-KMS instead of SSE-S3) for default encryption in the troubleshooting and temporary data bucket |
|
|
|
Updated 6 months ago
